Table of Contents
IP restriction, also known as IP filtering or IP whitelisting/blacklisting, is a security measure used to control access to a network or a specific resource based on the IP addresses of incoming requests.
In IP restriction, administrators specify a list of IP addresses or ranges that are either allowed (whitelisted) or denied (blacklisted) access to a particular system, service, or network. When a request is made to access the resource, the system checks the incoming IP address against the list of allowed or denied addresses.
Here’s how IP restriction works:
- Whitelisting: Only IP addresses that are included in the whitelist are allowed to access the resource. All other IP addresses are denied access.
- Blacklisting: IP addresses that are included in the blacklist are denied access to the resource. All other IP addresses are allowed access.

IP restriction is commonly used for various purposes including:
- Enhancing security: By restricting access to trusted IP addresses, organizations can prevent unauthorized access to sensitive information or resources.
- Compliance requirements: Certain regulations or compliance standards may require organizations to restrict access to specific IP addresses.
- Mitigating attacks: IP restriction can help mitigate the risk of certain types of attacks, such as denial-of-service (DoS) attacks or brute force attacks.
- Controlling access to internal resources: Organizations may use IP restriction to control access to internal systems, applications, or databases from external networks.
However, it’s worth noting that IP restriction alone may not provide comprehensive security, as IP addresses can be spoofed or dynamically assigned. Therefore, it is often used as part of a broader security strategy that includes other measures such as authentication, encryption, and monitoring.
Advantages of IP Restriction:
- Enhanced Security: IP restriction helps enhance the security of your network or resources by limiting access to authorized IP addresses only. This reduces the risk of unauthorized access, data breaches, and malicious activities.
- Controlled Access: With IP restriction, you have greater control over who can access your network, website, or specific resources. This allows you to enforce access policies and ensure that only trusted users or devices can connect.
- Compliance Requirements: Many industries and regulatory bodies require organizations to implement access controls and security measures to protect sensitive information. IP restriction helps organizations meet compliance requirements by controlling access to critical resources.
- Mitigation of Attacks: IP restriction can help mitigate various types of attacks, such as Distributed Denial of Service (DDoS) attacks, brute force attacks, and unauthorized access attempts. By blocking or whitelisting specific IP addresses, you can reduce the risk of these attacks succeeding.
- Customization: IP restriction allows you to customize access policies based on your organization’s specific needs and requirements. You can whitelist trusted IP addresses and block suspicious or malicious ones to tailor your security measures accordingly.
Disadvantages of IP Restriction:
- Limited Flexibility: IP restriction relies on static IP addresses, which may not be suitable for environments where users have dynamic IP addresses or access resources from multiple locations. This can limit flexibility and make it challenging to manage access for remote users.
- Potential for False Positives: In some cases, legitimate users may be denied access if their IP address is blocked or restricted incorrectly. This can lead to user frustration, decreased productivity, and support overhead as users seek assistance to resolve access issues.
- IP Spoofing: IP addresses can be spoofed or manipulated by attackers to bypass IP restrictions and gain unauthorized access to resources. While IP restriction provides a basic level of security, it may not be effective against sophisticated attacks that involve IP spoofing techniques.
- Administration Overhead: Managing IP restriction lists can be time-consuming, especially in large organizations with numerous users and devices. Administrators must regularly review and update the IP restriction lists to ensure they remain accurate and up-to-date.
- Single Point of Failure: IP restriction serves as a single point of failure in your security infrastructure. If an authorized IP address is compromised or if the restriction mechanism fails, attackers may gain unrestricted access to your network or resources.
Steps to Block a Specific IP Address:
First, log in to your cPanel account.
Go to the “Security” page and select “IP Blocker” from the drop-down menu.
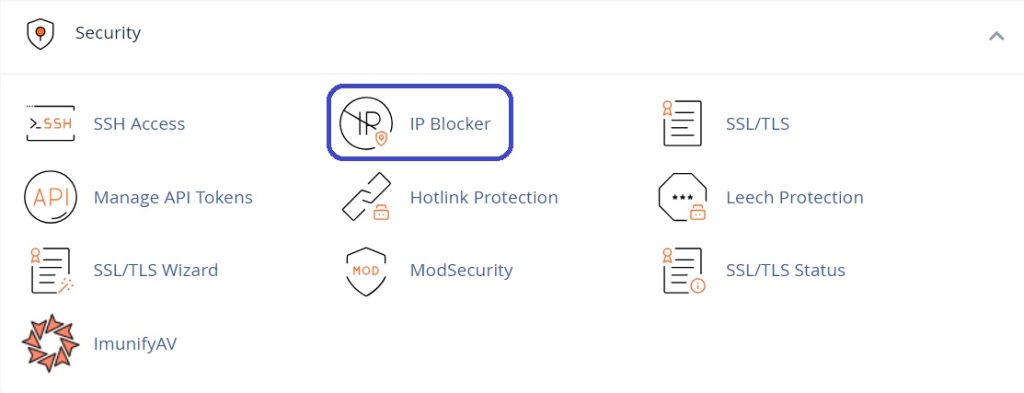
Add the domain name or range of IP addresses to the IP Address or Domain text field and click the Add button.
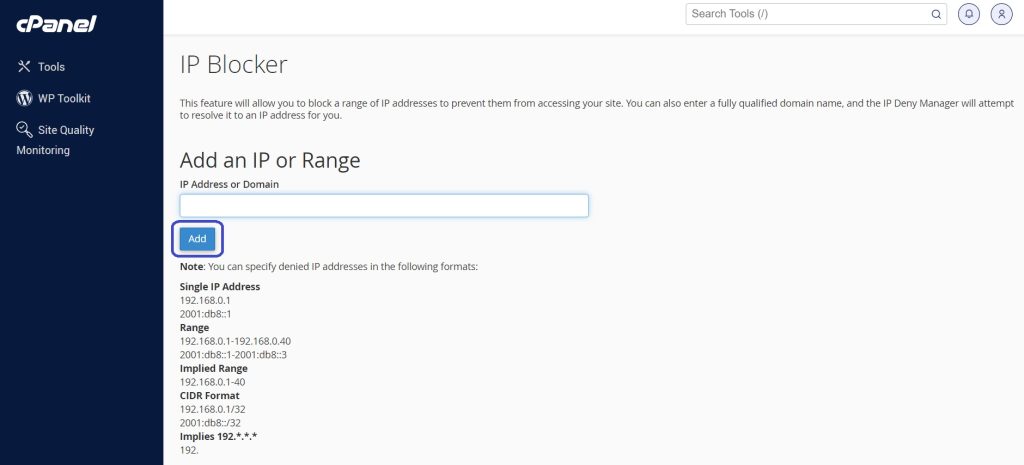
You will get a congratulatory message while completing the process.
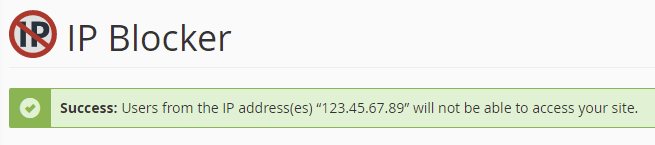
The IP address that has been added would be unable to access your website.
Steps to unblock IP address:
Open cPanel and log in.
Go to the “Security” page and select “IP Blocker” from the drop-down menu.

To unblock a specific IP address, click the Delete symbol under “Currently-Blocked IP Addresses”.

When requested for confirmation, click the Remove IP button, and a success message will appear.
The IP address that was temporarily banned can now access your website.
In this way, you can block or unblock a specific IP address or domain.
Here’s how IP restrictions typically work:
- Access Control List (ACL): An Access Control List is a list of rules that define which IP addresses are allowed or denied access to the resource. These rules can be configured at various levels, such as network routers, firewalls, web servers, or application servers.
- Whitelisting and Blacklisting: IP restrictions can be implemented using whitelisting or blacklisting techniques.
- Whitelisting: In whitelisting, only IP addresses that are explicitly allowed in the access control list are granted access to the resource. All other IP addresses are denied by default.
- Blacklisting: In blacklisting, specific IP addresses or ranges are explicitly blocked or denied access to the resource. All other IP addresses are allowed access by default.
- Configuring IP Restrictions:
- Firewalls: Network firewalls can be configured to block or allow traffic based on the source and destination IP addresses. Firewall rules can be set up to restrict access to specific ports or services based on IP addresses.
- Web Servers: Web servers, such as Apache or Nginx, can be configured to restrict access to websites or directories based on IP addresses. This can be achieved using configuration directives like “Allow” and “Deny” in Apache’s .htaccess files or Nginx configuration files.
- Application Servers: Application servers and web applications can implement IP restrictions programmatically by checking the IP address of incoming requests against a whitelist or blacklist. Access can be granted or denied based on the result of this check.
- Handling Access Requests:
- When a connection request is made to the network, server, or resource, the system checks the source IP address against the access control list.
- If the IP address is included in the whitelist and not in the blacklist, the connection is allowed, and the user gains access to the resource.
- If the IP address is included in the blacklist or not included in the whitelist, the connection is denied, and the user is blocked from accessing the resource.
- Logging and Monitoring: IP restrictions can be supplemented with logging and monitoring mechanisms to track access attempts, identify unauthorized access attempts, and detect potential security threats.
